From Malware Discovery to Victim Notification
Super appreciate of SANS ICS for hosting, check out my slides here!
Introduction
Part of my responsibilities at Dragos include threat hunting in public malware repositories such as VirusTotal. During an investigation into ICS/OT related filenames submitted from geopolitical hot bed zones, one file immediately caught my eye.

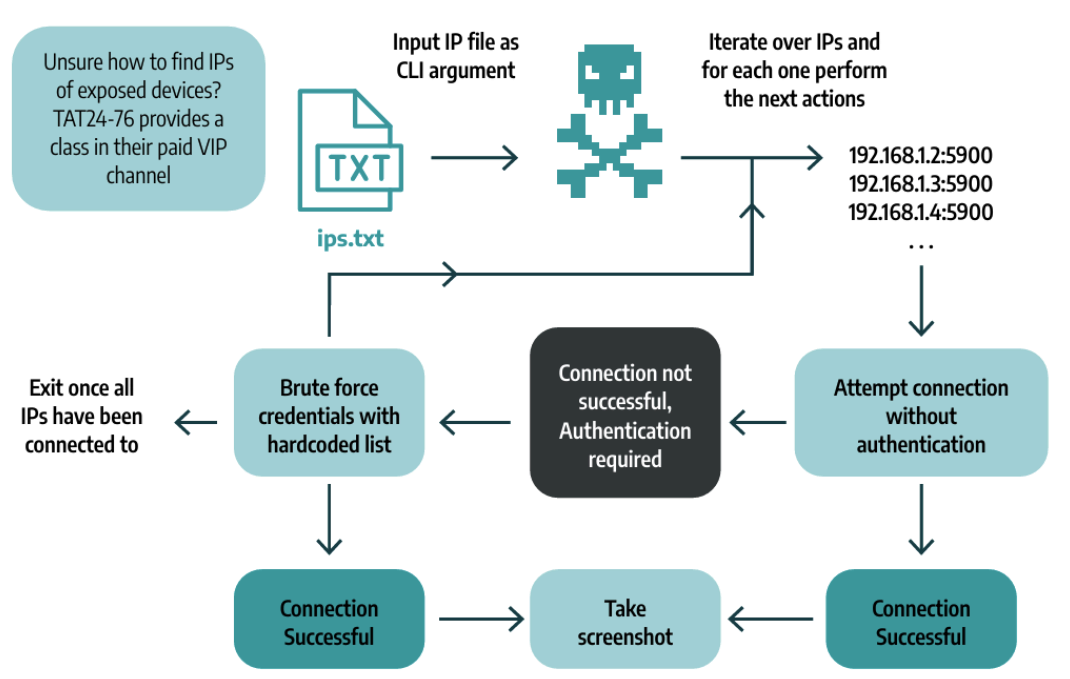
I will cover in more detail below, but this binary is essentially a VNC client application with basic brute forcing capabilities. Provided a list of IP addresses, KurtLar_SCADA attempts connection of each one. If authentication is required, KurtLar_SCADA will brute force the credentials with a small list of default credentials hardcoded in the binary. Once successfully authenticated, the tool takes a screenshot and saves it, proving it has access to the system.
The Telegram Channel
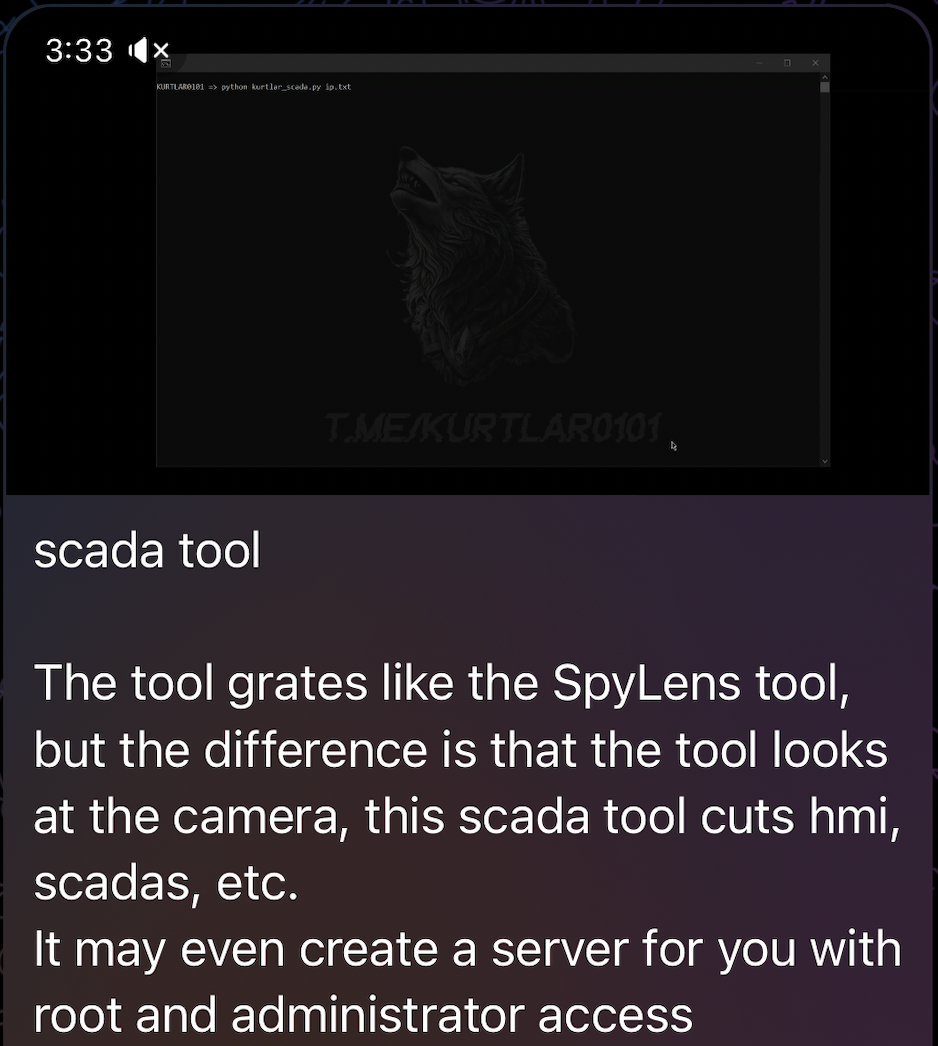
During investigation, we discovered a Telegram channel advertising their tools, exploits, database dumps, hacking courses, and more. The administrator behind the channel boasts pro-Iranian and anti-Western ideology, expressing their interest in hacking US or Israeli industrial systems (even offering discounts to those targeting USA/IL).
Here’s one of their Telegram messages advertising their tool:
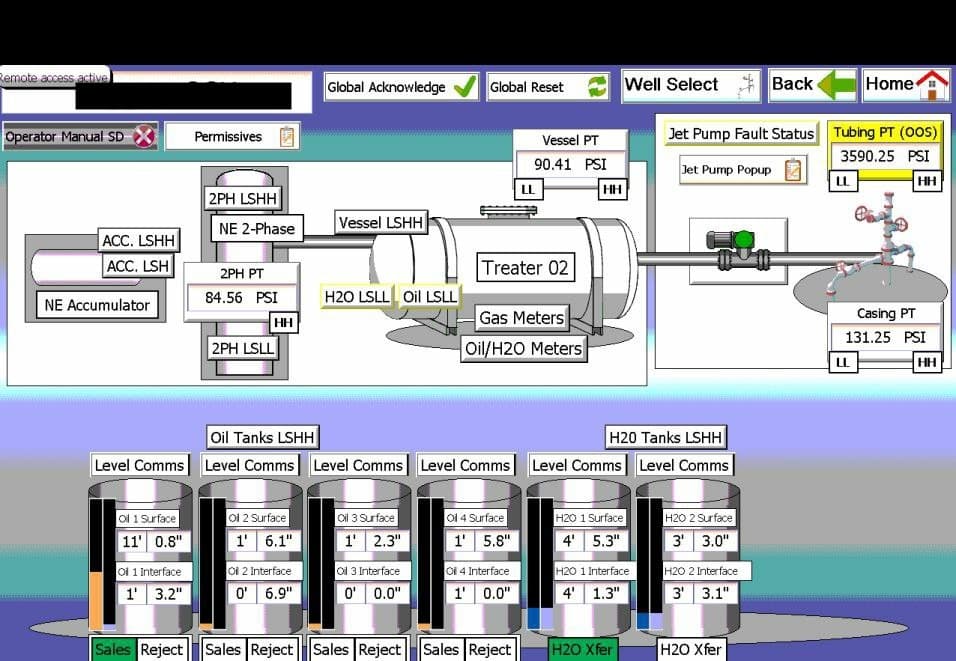
To prove their tool works, they provide multiple screenshots of compromised HMI screens, as demonstrated by the following US-based HMI:
There’s even a video of the developers using and compromising HMIs:
Malware Analysis of a Compiled Python Binary
Analyzing the malware was a unique challenge. KurtLar_SCADA is written in Python3.12, then compiled into a Windows binary via PyInstaller. For readers unfamiliar with compiled python, this is a mechanism to bundle the CPython interpreter with Python bytecode (an intermediate representation of your original source code). Fortunately, compiled python binaries can be decompiled into original Python source code, no IDA Pro license necessary!
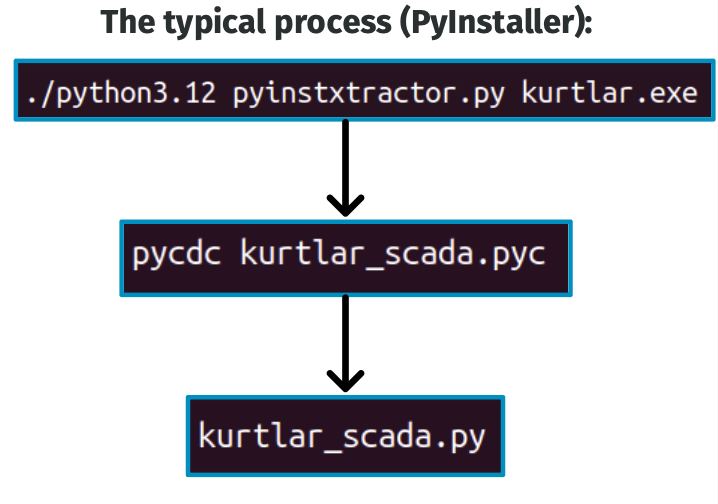
Unfortunately, since it’s Python3.12, there’s quite literally not a single decompilation tool available that covers Python3.10+. However, this does not mean we are completely stuck.
Using pycdas, a sibling tool to pycdc, we can obtain the bytecode’s disassembly which enables (painful) static analysis of the bytecode (similar to traditional static analysis of x86). There are some obfuscation layers to defeat, however most (except for symbol obfuscation) are trivial.
Defeating Obfuscation Layers
In one of the binaries, a marshalled Python code object is used to hide the contents from detections capabilities like Yara. Here’s an example of what this looks like:
import marshal
min = b'\xe3\x00\x00\x00<PYTHON_BYTECODE>\xde\x01\x00\x00'
ob = marshal.loads(min)
exec(ob)Essentially, this script embeds another Python script inside of it - the min variable contains the payload to be executed on line 6. This is easily defeated by modifying the script to instead format the bytecode into a valid PYC file representation and simply writing to disk:
import marshal
import importlib
min = b'\xe3\x00\x00\x00<PYTHON_BYTECODE>\xde\x01\x00\x00'
ob = marshal.loads(min)
#exec(ob) # ALWAYS COMMENT THIS LINE OUT!
bytecode = importlib._bootstrap_external._code_to_timestamp_pyc(ob)
with open("./kurtlar_scada.pyc", "wb") as pyc_file:
f.write(bytecode)Using a combination of static analysis of the bytecode disassembly, as well as leveraging LLMs like ChatGPT/PyLingual, we can slowly decipher it’s execution flow. Perhaps in a future blog I will cover compiled python and bytecode more in detail, but for another day!
Alerting the Victims
Leveraging Dragos’ OT-CERT, we made contact with CISA and a couple other external parties. Through these relationships, we informed 3 victims of their compromised, exposed, and poorly secured assets. The responses ranged from gratitude (and further leveraging CISAs services) to indifference. ‘Tis the name of the game, you can lead a horse to water but you can’t force it to drink.
Conclusion
KurtLar_SCADA is another example of low-skilled, opportunistic hacktivists leveraging “low-hanging fruit” techniques. This is a threat the should not be hyped. However, these techniques are still effective if you leave HMIs exposed to the internet and poorly secured. Please use a VPN, do not port forward remote access services like VNC.
This type of activity could be reduced significantly if vendors were incentivized to care about security. One of vendors who produced the software which was compromised by KurtLar_SCADA had this to say on their VNC security page…
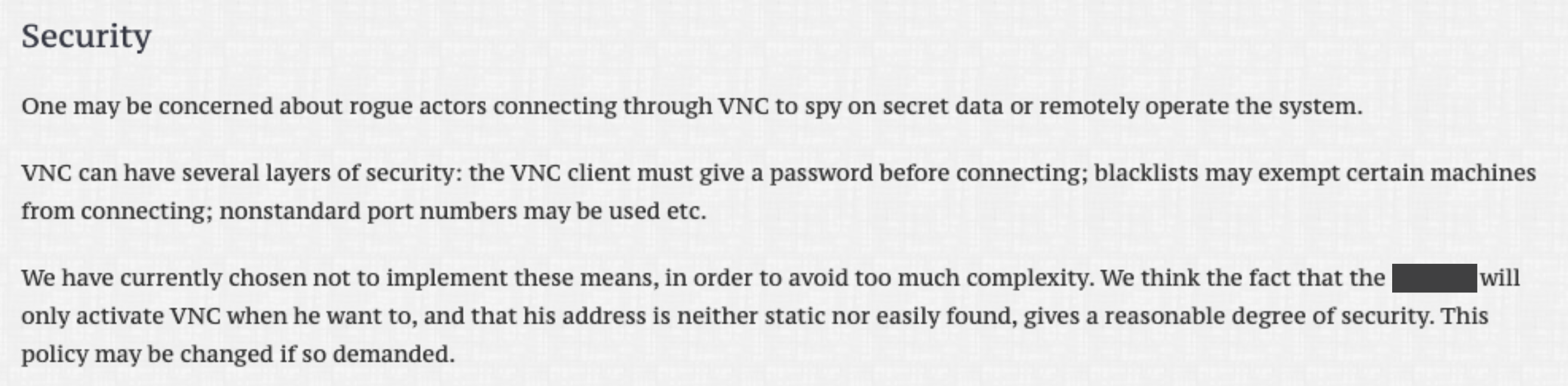
Folks - please so demand.